Boost Business Intelligence with Powerful Data Security Solutions

In today’s rapidly evolving digital landscape, robust data security practices have become a requirement, even law. When approaching data analytics, companies need to ensure that their own data, as well as customers’, is 100% protected at all times. This article covers the importance of data security in business intelligence and the multiple security features of Bold Reports®.
The importance of data security in business intelligence
Data security is critical in business intelligence for:
Protecting of Sensitive Information
BI systems often handle sensitive data, including customer information, financial records, and proprietary business strategies. Ensuring this data is secure prevents unauthorized access, theft, or leakage, which can lead to significant financial losses and damage to a company’s reputation.
Maintaining Data Integrity
Data security measures protect data sources against unauthorized alterations, ensuring the integrity and reliability of the data used in BI processes. This helps maintain trust in the analytics and insights generated.
Preventing Financial Losses
A data breach can cost a company big, from fines and legal fees but also the loss of business, damage to its brands’ reputation, and the expense of remediation efforts. By prioritizing data security, businesses can avoid these financial pitfalls.
Enhancing Customer Trust
Effective data security practices help build and maintain trust with customers and investors. A breach can severely damage customer confidence, while proving that your security is tight can boost it.
Ensuring Business Continuity
Cyber-attacks and data breaches can disrupt business operations, leading to downtime and loss of productivity. Strong data security measures, including backup and disaster recovery plans, ensure that businesses can quickly return to operating smoothly, even in the face of such threats.
Preventing Insider Threats
Not all data breaches come from external threats; employees or contractors can also pose a significant risk, sometimes purposefully, sometimes accidentally. Implementing stringent access controls, monitoring, and auditing mechanisms helps mitigate the risk of insider threats.
Data security in Bold Reports
Bold Reports is not just any reporting tool; it’s a cutting-edge solution designed specifically to meet the business intelligence demands of modern, security-minded businesses.
Key Data Security Features of Bold Reports
Encryption
Bold Reports employs advanced encryption techniques to secure sensitive data like passwords and database details. It uses Rijndael Encryption (256 bits), RSA Cryptography (1024 bits), and AES Cryptography (128 bits) encryption methods to encrypt these details. Each time a user installs a Bold Reports product, a private key is generated for the customer’s machine to encrypt the data.

Single Sign-On (SSO)
Bold Reports supports SSO integration with identity providers like Office 365, OAuth 2.0, and OpenID, allowing users to log in and access their accounts with a single set of credentials.

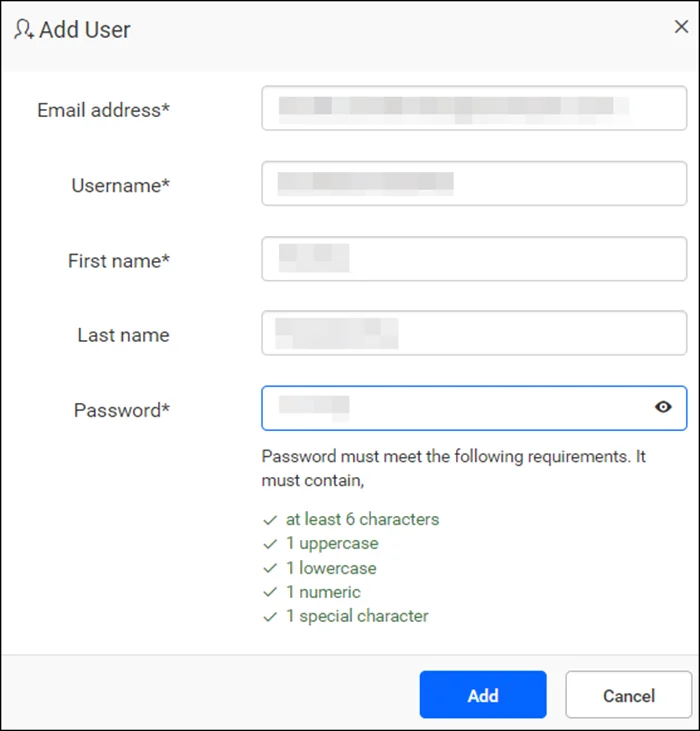
Password Policies
Bold Reports enables organizations to establish and enforce password policies to ensure secure and strong passwords. These policies, which can be customized to align with specific IT requirements, include rules for password rotation frequency and expiration, helping organizations meet their security standards.
IP Restrictions
Bold Reports allows organizations to restrict report access based on IP addresses, ensuring that only authorized users or domains can access the reports.
Secure Data Transfer and Compliance
Bold Reports ensures the secure transfer of data by utilizing the HTTPS protocol for all communications and Transport Layer Security (TLS 1.2/1.3) encryption for internal API calls. This ensures that customer data is handled in accordance with the highest standards of data protection.
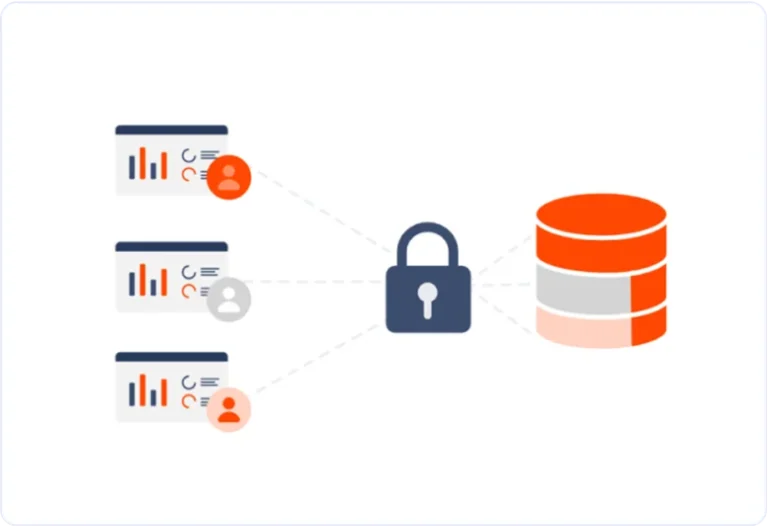
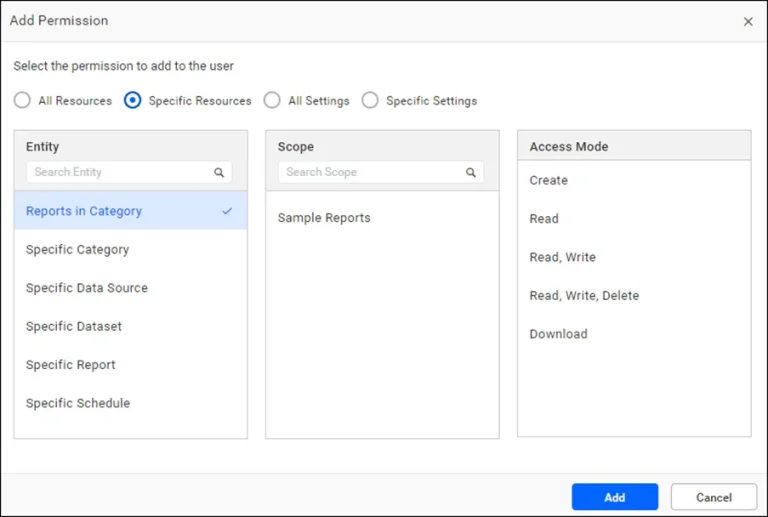
Granular Permissions and Secure Cloud Hosting
Bold Reports provides a secure platform for business intelligence operations by combining granular permissions with secure hosting options. This system allows organizations to control access to reports, data sources, and datasets, ensuring only authorized users can access sensitive data. Bold Reports can be hosted on secure
Conclusion
Data security forms the cornerstone of effective business intelligence, ensuring the protection, integrity, and trustworthiness of critical information. By adopting Bold Reports® as their BI platform, businesses can safeguard their data assets, maintain compliance, and empower informed decision-making with confidence. Implement secure business intelligence today with Bold Reports and stay ahead.
Visit the Bold Reports website for more information, or sign up for a 30-day free trial to experience the power of Bold Reports firsthand.
If you have any questions, please post them in the comments section. You can also contact us through our contact page or, if you already have an account, you can log in to submit your support question.